The simplest way to make locally-trusted certificates is to use mkcert, a simple zero-config tool.
Assuming a macOs machine, the process is the following:
Install mkcert:
brew install mkcert
brew install nss # required if we're using firefox
Install the local CA in the system trust store
mkcert -install
Generate the certicate for any names you'd like. Here I'm generating one for newsletter.local
mkcert -cert-file fullchain.pem -key-file privkey.pem newsletter.local
Point the new name to the local address in the hosts(/etc/hosts) file if it doesn't exist already
127.0.0.1 localhost newsletter.local
fe80::1%lo0 localhost
::1 localhost
Here we're loading the certificates in nginx:
server{
# ipv6
listen [::]:443 ssl http2 ipv6only=on;
# ipv4
listen 443 ssl http2;
server_name newsletter.local;
ssl_certificate /var/www/newsletter.place/fullchain.pem;
ssl_certificate_key /var/www/newsletter.place/privkey.pem;
root /srv/newsletter.place/src/public;
index index.html;
}
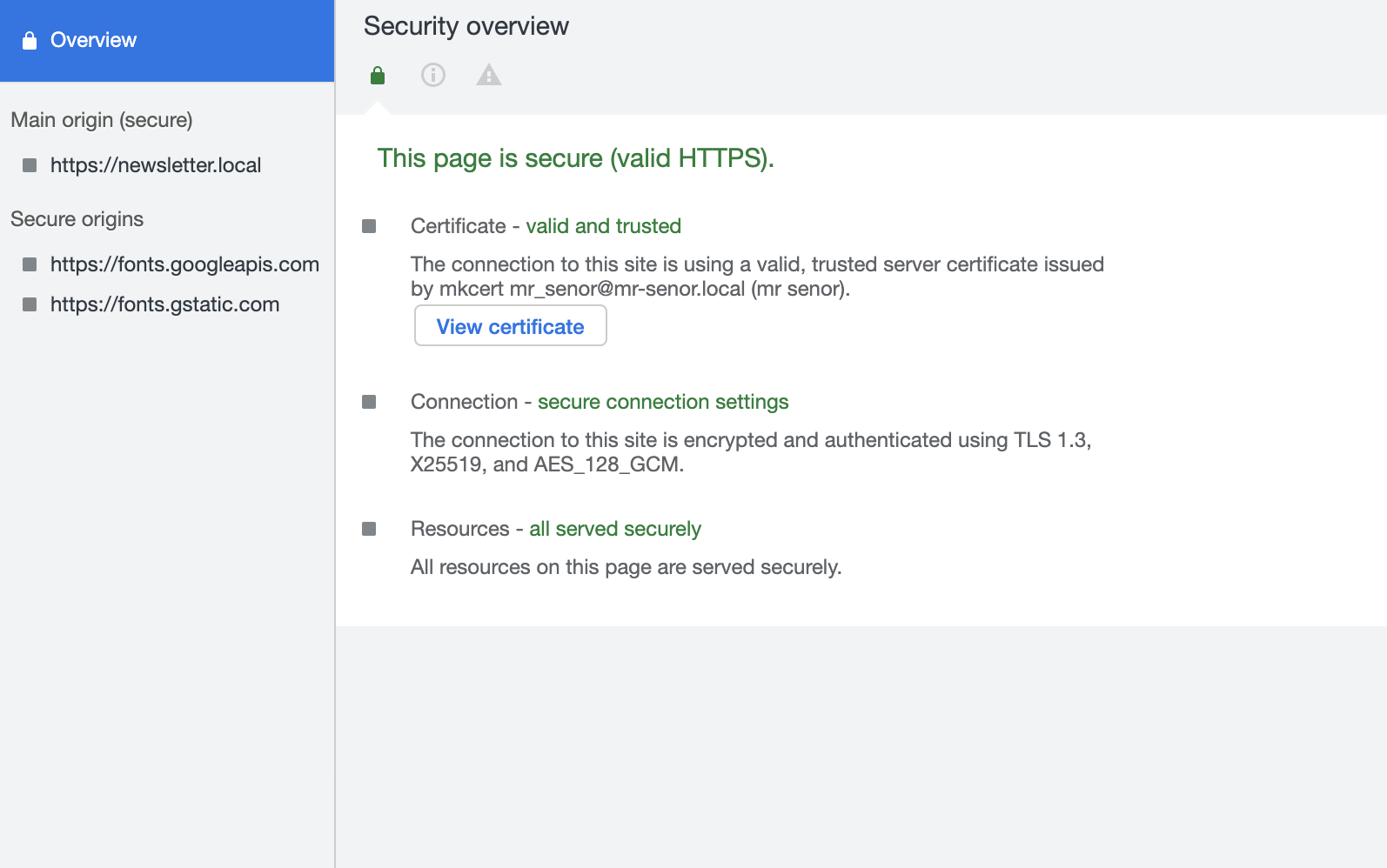
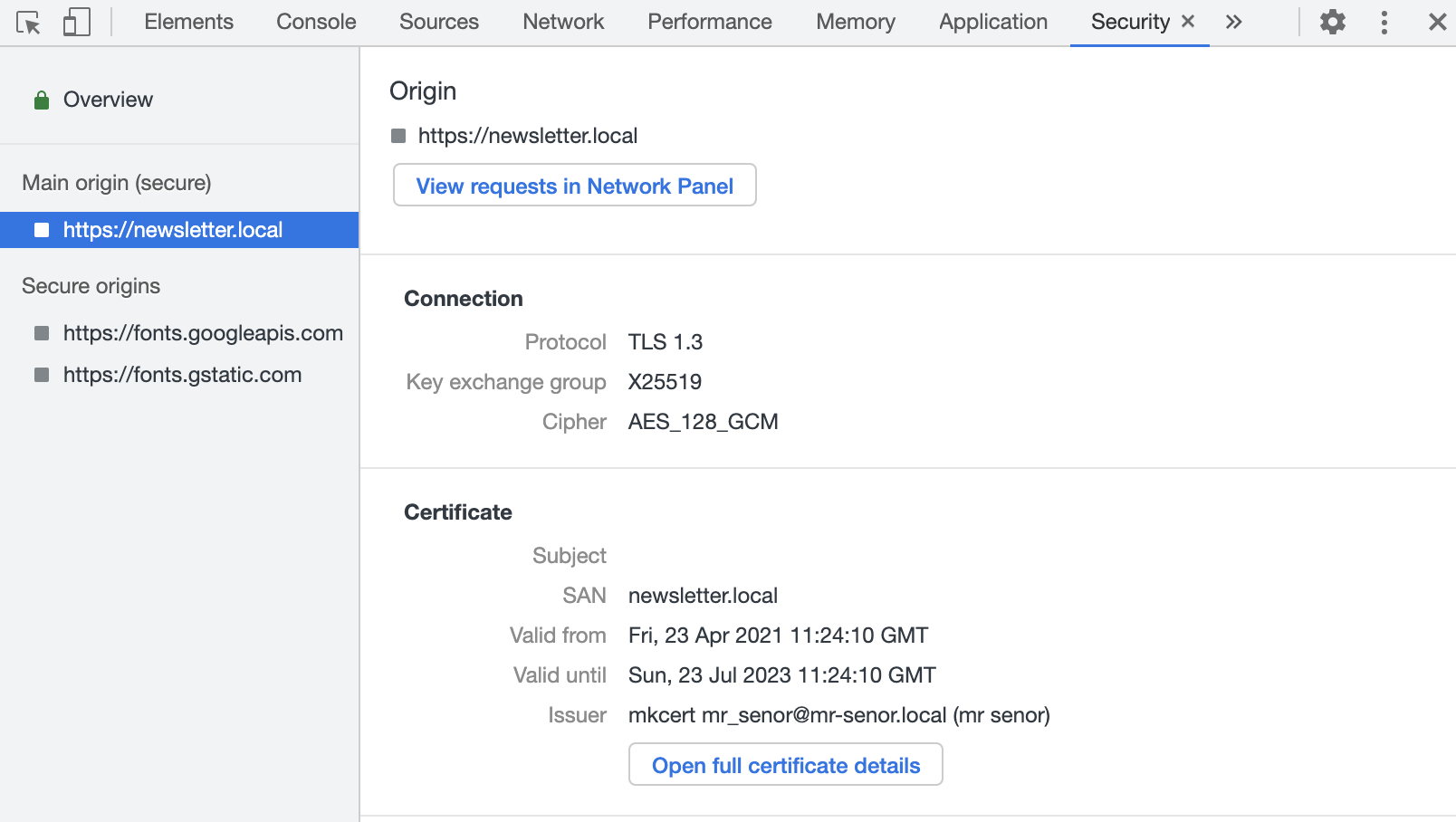
Assuming everything was set up correctly we can now see that https://newsletter.local is now using a locally-trusted self-signed certificate, and it's valid for two years.