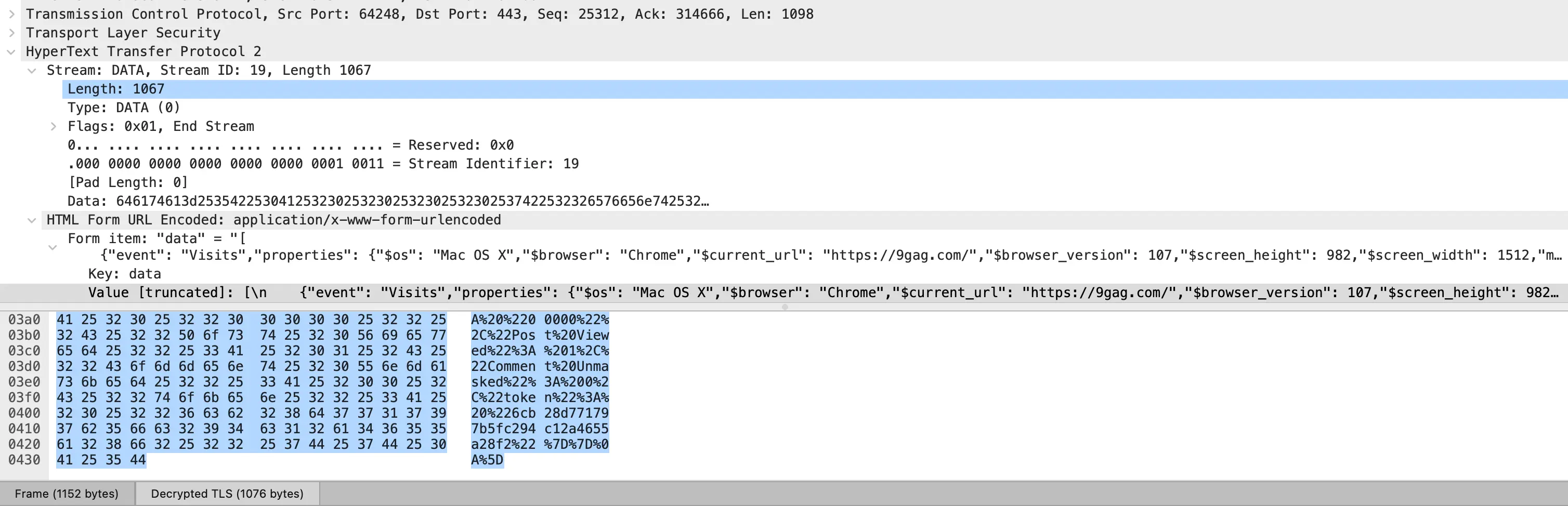
Browser traffic
To decrypt HTTPS, HTTP2 and HTTP3 over Quic traffic, we basically need to make the system store the TLS session keys(used by the browser when doing the TLS handshake to encrypt all data) on a file so we can then load it into Wireshark.
We can tell the system to store the SSL keys by exporting the following env key:
export SSLKEYLOGFILE=~/.ssl-keys.log
Next, we open a browser that supports saving the TLS keys on file(eg: Chrome), and navigate to a website using HTTPS to confirm the sessions keys being stored in our file. We can cat the file to verify:
cat $SSLKEYLOGFILE
"...: No such file or directory" error is likely since the system/browser is not using the env key yet.
In this case, launching the browser in the same window we exported SSLKEYLOGFILE helps, like so:
open /Applications/Google\ Chrome\ Canary.app/
After verifying the keys are being stored properly on a file, it's time to make Wireshark use the file to decrypt the traffic: we need to go into Wireshark > Preferences > Protocols > TLS, and add our ~/.ssl-keys.log file in the (Pre)-Master-Secret log filename file input. We should now be able to the see the decrypted data.